Below is a review of the NIS 2 Directive and, practically, what it means for businesses operating in the EU.
NIS 2 Timeline and Implementation
As an EU directive, NIS 2required implementation by individual EU Member States byOctober 17, 2024, i.e., they had to adopt national laws in line with NIS 2 by this date. However, only a relatively small number of Member States met this deadline. One way to track implementation is through the European Commission’s website here.
For companies with a pan-footprint in the EU, it’s essential to track the progress of implementation across the EU, as differing national requirements may impact compliance efforts.
In July 2024, the European Commission also issued an Implementing Regulation, effective from October 2024, that specifies detailed security and reporting requirements for the following digital providers:
- DNS service providers;
- top-level domain name registries;
- cloud-computing service providers;
- data center service providers;
- content delivery network providers;
- managed service providers;
- managed security service providers;
- providers of online marketplaces, online search engines and social networking services platforms; and
- trust service providers.
For entities in scope, this Regulation provides more granular cybersecurity obligations, directly impacting operational and reporting standards.
Expanded Scope: Who Is in Scope Under NIS 2?
Unlike its predecessor, NIS 2 uses a more prescriptive approach to determine which organizations fall under its remit. Compliance applies to entities that meet three conditions:
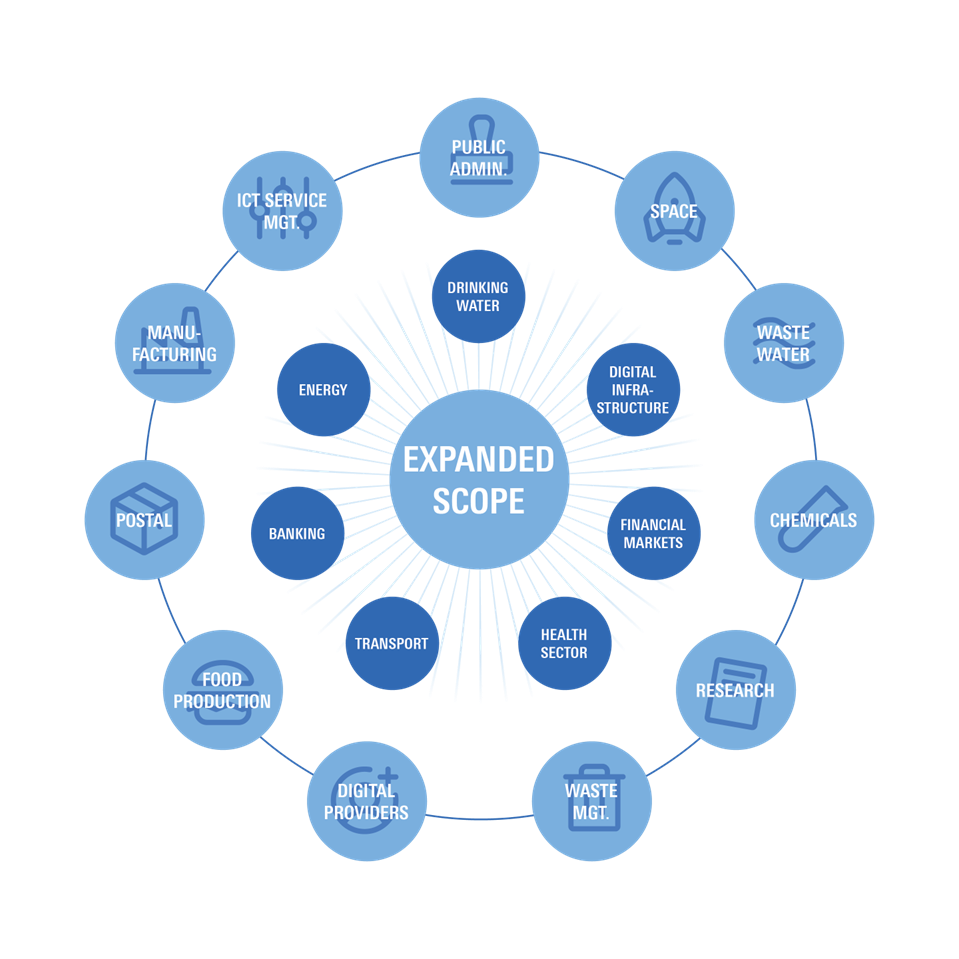
1. Sector Requirements: NIS 2 applies to organizations operating in sectors listed in Annexes 1 and 2.
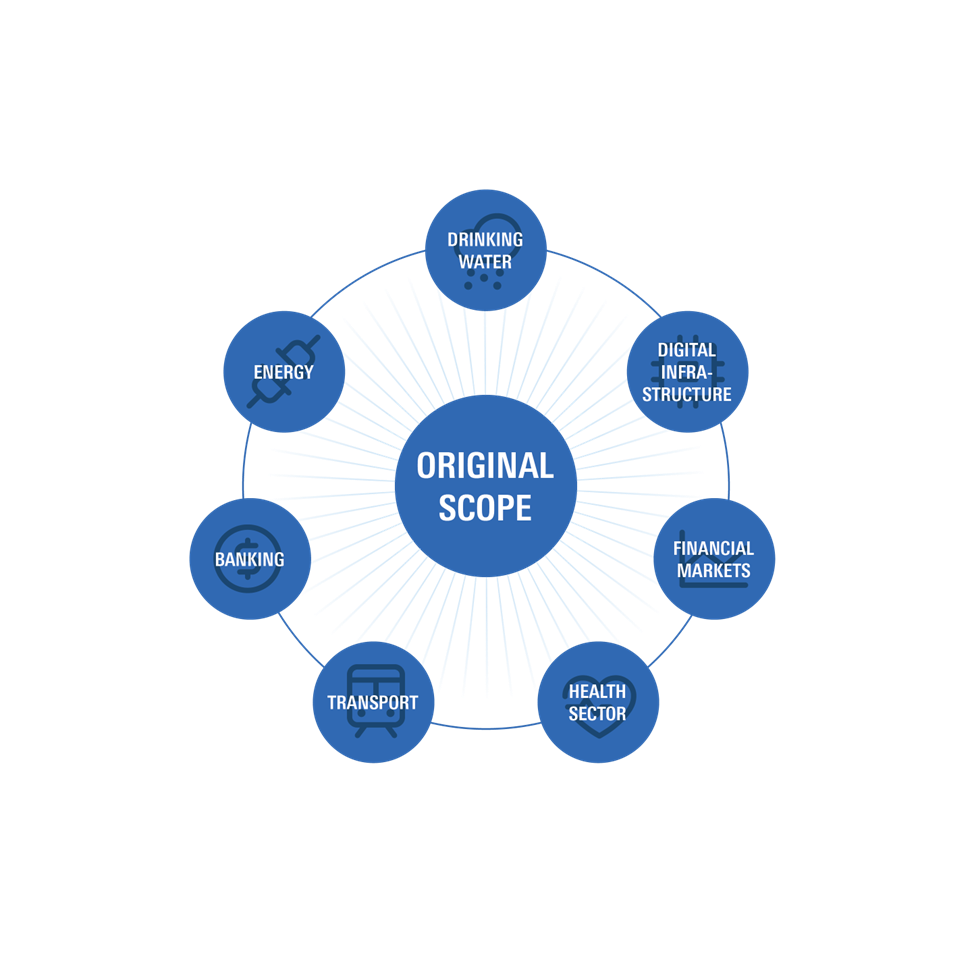
Sectors in scope of NIS 1:
Sectors in scope of NIS 2:
2. Size Requirements: NIS 2 targets medium to large enterprises with more than 50 employees or a balance sheet exceeding €10 million.
3. EU Presence: Organizations providing services or conducting business in the EU are within scope.
Further, NIS 2 distinguishes between “essential” and “important” entities, with each facing different levels of regulatory scrutiny and potential penalties. Broadly speaking, any “large entities” operating in Annex 1 sectors will be considered “essential” i.e., they either have more than 250 employees or an annual turnover or an annual balance sheet exceeding €50 million. Other entities are also considered “essential” regardless of size, such as (among others) top-level domain name registries or other digital providers. All entities that are not “essential” are considered “important”; this includes those operating in Annex I sectors that are not “large entities”.

Jurisdiction and Territoriality
One of NIS 2’s complexities lies in jurisdiction. Generally, organizations are within the jurisdiction of the Member State in which they are established. However, entities operating across multiple EU Member States may face concurrent jurisdiction, requiring careful coordination with authorities in each relevant Member State.
For digital providers identified above, a one-stop-shop model applies, where the “main establishment” determines which Member State has jurisdiction. The main establishment test under NIS 2 has a hierarchical approach to establish which Member State will hold primary regulatory responsibility:
1. Primary Test – Decision-Making Location
The first test examines where the primary decisions related to cybersecurity risk management are made. This is generally the location where the organization’s leadership oversees the implementation of cybersecurity measures, policies and compliance protocols. If a Member State can clearly be identified as the primary site of these decisions, it will serve as the "main establishment" under NIS 2.
2. Secondary Test – Operational Control Location
If it is unclear where the main cybersecurity decisions are made, or if these decisions are managed from outside the EU, the secondary test applies. This considers the Member State where the entity conducts most of its cybersecurity operations. For instance, this could include the location of key data centers, security operations centers, or other infrastructure critical to the organization’s cybersecurity functions.
3. Final Test – Employee Count Location
If neither the decision-making location nor the primary operations location is clear, a third test applies. In this case, the main establishment is determined by the Member State with the highest number of employees. This provides a practical fallback to identify the jurisdiction, ensuring regulatory oversight even when other factors are indeterminate.
For digital providers headquartered outside the EU but offering services within the EU, NIS 2 mandates the appointment of an EU representative. This representative must be based in a Member State where services are provided and will act as the point of jurisdiction for regulatory matters. In the absence of a designated representative, any Member State where the services are offered can exercise jurisdiction over the provider.
Registration and Security Obligations
I. Registration Requirements
There are two registration requirements. First, Member States have until April 17, 2025, to create a list of “essential” and “important” entities in their jurisdiction. To do this, they must require entities to register and provide certain information needed to compile the list. The deadline for registration will vary by Member State. For example, the deadline in Belgium is March 18, 2025.
There is also a separate register for digital providers mentioned above. This must be stood up by January 17, 2025. Again, the deadline for registering will vary by Member State. For example, the deadline in Belgium is December 18, 2024.
II. Required Security Measures
Under NIS 2, organizations must implement technical, operational and organizational security measures proportionate to the risk level. NIS 2 requires oversight from management bodies, who must be trained on, and take responsibility for, cybersecurity measures. The Implementing Regulation introduces specific security measures like multifactor authentication, asset inventories, secure development life cycle practices and environmental controls. These provide a minimum compliance benchmark under NIS 2 for the digital provider mentioned above.
A significant focus on supply chain security also features in NIS 2, emphasising third-party security assessments and incorporating cybersecurity clauses in supplier contracts.
Some Member States offer frameworks, like Belgium’s “Cyberfundamentals Framework” (CyFun), which support organizations in demonstrating compliance through recognized certifications.
Under Article 4, NIS 2 obligations may not apply if sector-specific laws meet or exceed NIS 2 requirements. The European Commission has issued guidance clarifying the application of Article 4 listing the sector-specific laws that the Commission considers fall within scope. Regulation 2022/2554, the Digital Operational Resilience Act (DORA), is the only law currently identified, although the guidance states that the fact a law is not listed does not necessarily mean that it does not fall within scope of Article 4. This means that banking and financial entities subject to DORA are exempt from some NIS 2 requirements. (See our earlier alert here.)
III. Incident Reporting
NIS 2 requires essential and important entities to notify the relevant Member State authority of any incident that has a “significant impact” on the provision of their services or on the recipients of those services. This includes any incident that: (a) has caused or is capable of causing severe operational disruption of the services or financial loss for the entity concerned; or (b) has affected or is capable of affecting other natural or legal persons by causing considerable material or non-material damage.
Incident reporting requirements under NIS 2 adopt a tiered notification system:
- Early Warning (24 hours): A preliminary notification to relevant authorities, indicating if the incident is malicious or has cross-border implications.
- Incident Notification (72 hours): An assessment of severity and impact.
- Final Report (One month): A final comprehensive report detailing the incident’s cause, impact and response.
What amounts to a “significant impact” and the reporting timeframes can be varied by each Member State (including on a sector-specific basis), so it is important to track EU-wide implementation.
Incidents reportable under NIS 2 may also trigger a notification under the General Data Protection Regulation 2016/679 (GDPR), underscoring the importance of a consolidated incident response plan that aligns GDPR, NIS 2 and any other obligations (such as the Directive 2002/58/EC (the ePrivacy Directive) and/or DORA).
Enforcement and Penalties
NIS 2 has introduced a stricter enforcement framework, granting authorities extensive oversight powers, including audits and the right to suspend certifications. Fines differ based on the classification of the entity:
- “Essential” entities face potential fines of up to €10 million or 2% of global turnover.
- “Important” entities can be fined up to €7 million or 1.4% of global turnover.
Notably, management can be held personally accountable, with the potential for executive bans in cases of serious non-compliance.
Key Practical Steps for NIS 2 Compliance
- Determine Applicability. Identify if your organization falls under NIS 2, and if so: (i) whether it is classified as an “essential” or “important” entity, and (ii) the relevant jurisdictional scope.
- Reporting Requirements. Identify applicable reporting requirements and deadlines.
- Review and Map Requirements. Assess the specific obligations (cyber risk management, incident reporting) that apply and consider differences across applicable Member States.
- Conduct a Gap Analysis. Audit current security and incident response measures to identify gaps relative to NIS 2 requirements.
- Consider Wider Legislative Landscape. NIS 2 should be considered alongside other similar obligations (e.g., GDPR, DORA, the EU’s Cyber Resilience Act etc.).
- Address Supply Chain Security. Extend new security controls and incident reporting obligations to suppliers, as required by NIS 2. Consider contract remediation.
- Implement Staff Training. Conduct regular training for staff at all levels to build cyber awareness and ensure compliance with NIS 2 and related cyber resilience laws.
Conclusion
NIS 2 signals a significant advancement in the EU’s cybersecurity posture, requiring a coordinated approach across jurisdictions and sectors. As implementation continues, organizations should consider NIS 2 within the broader regulatory landscape, such as GDPR and the upcoming DORA for financial services. The interplay of these laws underscores the importance of a robust cybersecurity strategy that meets EU standards and prepares organizations to navigate an increasingly complex regulatory environment.


